Managing cloud costs effectively requires more than just tracking usage. One of the foundational pillars of mature FinOps practices is accurate cost allocation. Without proper allocation, organizations lack visibility into which teams, applications, or environments are responsible for spend. This gap can make optimization efforts difficult, reporting imprecise, and accountability weak.
Tagging, when enforced correctly, solves this problem by enabling granular cost attribution across business units. But in dynamic environments where resources are created frequently and by multiple stakeholders, ensuring consistent tagging becomes challenging. This is where automation becomes essential.
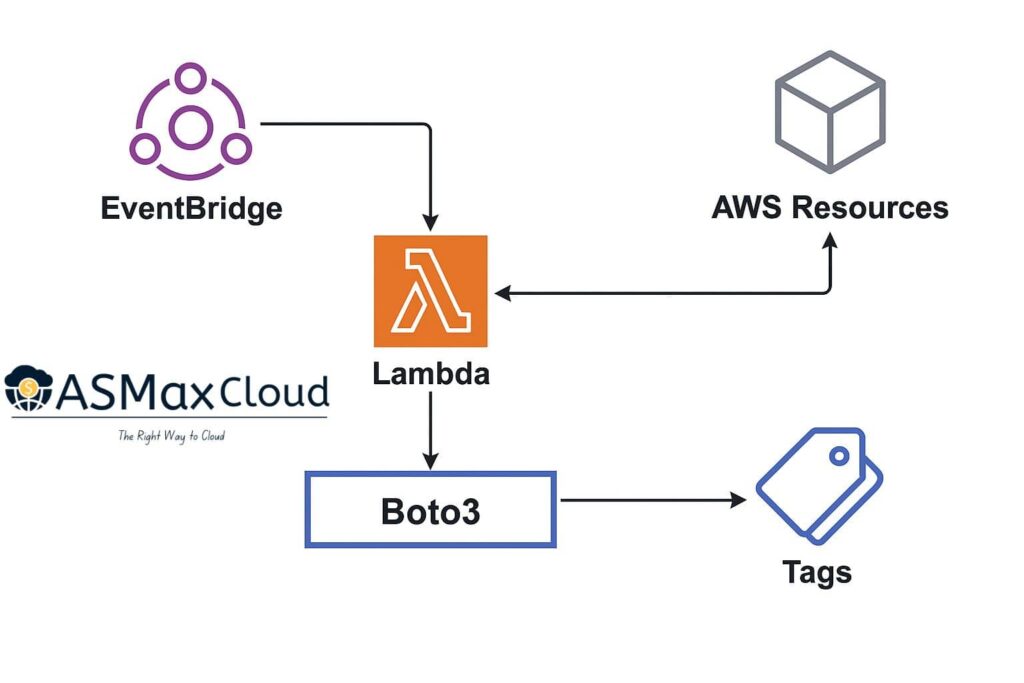
In this blog, I’ll walk through a practical approach to automating AWS cost allocation using resource tags, AWS Lambda, and Boto3. The implementation is aligned with FinOps best practices and designed to be extensible, secure, and production-ready.
Establishing a Tagging Strategy Anchored in Business Context
Before diving into the technical automation, it is important to recognize that tagging is not just a technical activity. It is a governance mechanism that connects cloud infrastructure to business objectives. A sound tagging strategy should emerge from collaboration across engineering, finance, and product teams.
Tags like Environment, Application, Owner, and CostCenter serve as the minimum baseline. But in FinOps-driven environments, tags such as BudgetCode, CustomerID, or ComplianceStatus often provide additional attribution fidelity. The key is to ensure that every tag serves a clear reporting or policy-enforcement purpose.
Enforcement should be aligned to cloud resource lifecycles. That means developers or CI/CD pipelines should not be able to deploy untagged resources. For infrastructure created manually or via ad-hoc scripts, guardrails become even more critical.
This is where a Lambda-based remediation system plays a central role—enabling continuous enforcement without blocking innovation.
Architecture of the Automated Tag Enforcement System
The architecture we will implement comprises four key components:
AWS Config Rule or EventBridge Trigger to detect untagged or mis-tagged resources in real time.
AWS Lambda Function written in Python using Boto3 to inspect and tag non-compliant resources.
Tag Policy or SCPs to define mandatory tag keys at the organizational level.
CloudWatch and SNS for logging and alerting.
For the scope of this blog, the focus is on the Lambda function and its integration with EventBridge to reactively tag resources.
The basic event-driven model works like this: when a resource is created or modified, EventBridge triggers the Lambda function. The function inspects the resource, checks for required tags, and either adds default tags, notifies the owner, or deletes the resource depending on the configuration.
This allows organizations to strike a balance between automation and control.
Writing the Lambda Function with Boto3
Below is a simplified but extensible version of the tagging remediation Lambda. This example focuses on EC2 instances, but the logic can be adapted to handle RDS, S3, Lambda, and more.
import boto3
required_tags = {
"Environment": "Undefined",
"CostCenter": "0000",
"Owner": "Unknown"
}
def lambda_handler(event, context):
ec2 = boto3.client('ec2')
instance_id = event['detail']['instance-id']
response = ec2.describe_tags(Filters=[{
'Name': 'resource-id',
'Values': [instance_id]
}])
existing_tags = {tag['Key']: tag['Value'] for tag in response['Tags']}
missing_tags = {}
for key, default in required_tags.items():
if key not in existing_tags:
missing_tags[key] = default
if missing_tags:
tag_list = [{'Key': k, 'Value': v} for k, v in missing_tags.items()]
ec2.create_tags(Resources=[instance_id], Tags=tag_list)
print(f"Added missing tags: {missing_tags}")
else:
print("All required tags are present.")
In a real-world scenario, this Lambda would be enhanced to handle cross-account resource tagging using STS, support exception lists, and perhaps integrate with a tag compliance dashboard for visibility.
This automation could be extended to monitor daily compliance rates, feed metrics into CloudWatch dashboards, and trigger alerts if tag compliance drops below a threshold. These insights help the FinOps team proactively engage with stakeholders and correct systemic issues early.
Deployment and Operationalization Using IaC
Deploying the Lambda manually is not ideal. It should be managed through Infrastructure-as-Code (IaC), either with CloudFormation or Terraform. This ensures the automation becomes part of your environment’s baseline posture and can be tracked and updated consistently across environments.
For example, with CloudFormation, you can define an EventBridge rule to capture RunInstances events and tie it to your Lambda. You can also define IAM permissions to scope down the Lambda’s privileges, ensuring it only accesses tagging APIs.
Integrating this system into your landing zone or organizational unit templates ensures that tagging compliance is not an afterthought but an embedded control.
Integrating Tag Enforcement into FinOps Reporting
Once the tagging enforcement system is operational, it becomes much easier to generate reliable chargeback or showback reports using AWS Cost Explorer, Athena, or custom CUR pipelines.
More importantly, consistent tagging unlocks the ability to apply FOCUS-aligned KPIs—such as cost per customer, cost per environment, and allocation coverage ratio. These KPIs form the backbone of modern FinOps reporting and help teams make informed trade-offs about performance, resilience, and cost.
In addition, organizations can now create dashboards to track tag coverage over time, investigate trends in tag compliance, and highlight services or teams that need coaching or process improvements.
Why You Need This?
Automating AWS cost allocation with tagging is not just a technical improvement—it is an operational enabler that drives better decisions, cleaner reporting, and cultural accountability. When paired with Lambda and Boto3, this automation becomes lightweight, scalable, and easy to integrate with existing workflows.
As cloud footprints grow, such automation becomes non-negotiable. FinOps teams that invest early in tagging governance and automation build a strong foundation for cost transparency and optimization at scale.
In future posts, I’ll explore how this automation can be expanded to multi-account environments, support exception management, and integrate with third-party tools like CloudHealth, Anodot, or CloudZero for a more holistic FinOps system.
